SIFF Overview
SIFF is a unified configuration management tool for all your infrastructure devices, systems, applications and services. Regardless of what is the source of the configuration data, whether it’s a physical or virtual device, or it’s a Cloud or SaaS API, as long as it’s textual in nature, SIFF can collect and monitor the configuration data for changes. From this rich source of configuration data, SIFF enables, interacts and drives many operational processes that were previously too resource and time consuming to automate.
SIFF Mission
Why is it important to collect and monitor configuration changes?
Our motto at SIFF is to help our customers answer the universal question:
What the #$%! changed
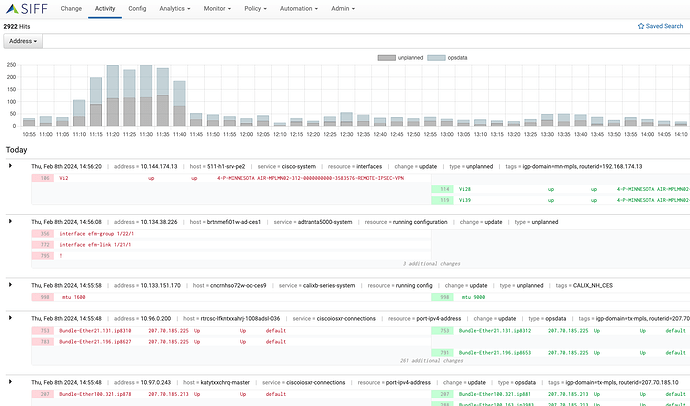
The ability to quickly identify recent changes and whether it relates to the current incident is essential to isolate and identify the root-cause of any problem. SIFF can help reduce the time looking up configuration data, see recent changes and how it relates to any planned or unauthorized changes.
Why is it important to collect from all sources?
Complex problems typically involve multiple functional domains, e.g. is the problem with the network, is it the application, is it security? These finger pointing and extended bridge calls waste a lot of resources. The ability to connect the dots by showing configuration changes in one place can dramatically improve the efficiency of operational support teams
How does this relate to Infrastructure as Code?
As IT and Operations being to view the infrastructure that they manage as “code”, by programmatic configuration changes and automation tools, for improved efficiency and reduced human error; SIFF addresses a key fundamental in software development processes that is often missing in IT and Operations - “Configuration Version Control”.
SIFF is like the GitHub for your infrastructure configuration data
What can you do with SIFF and the Configuration Data?
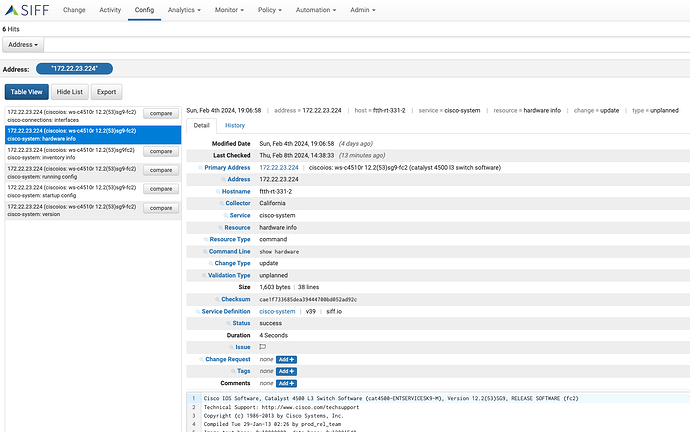
Search and Lookup configuration data
Avoid having to directly log into devices or swivel chair between different tools to lookup configuration information. All current configuration and history are available in one place.
Examine recent configuration changes to accelerate troubleshooting
Configuration change data is instrumental for real-time troubleshooting or post-incident forensic analysis. See before and after comparisons for a device as well as comparing configs between similar devices.
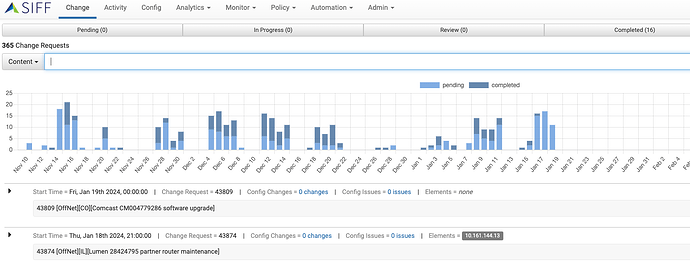
Identify Planned vs Unauthorized Changes
Using SIFF Change module or though integration with your ITIL / change management systems (e.g. ServiceNow), SIFF can identify planned changes vs unauthorized changes. As configuration changes are independently monitored by SIFF, they are correlated with the planned changes and automatically tagged with the change request number. This also enables post-implementation review of planned changes to proactively identify any potential human errors as well un-intended automation errors. More importantly, unauthorized changes that circumvented the change process can be analyzed to determine whether they pose a security risk.
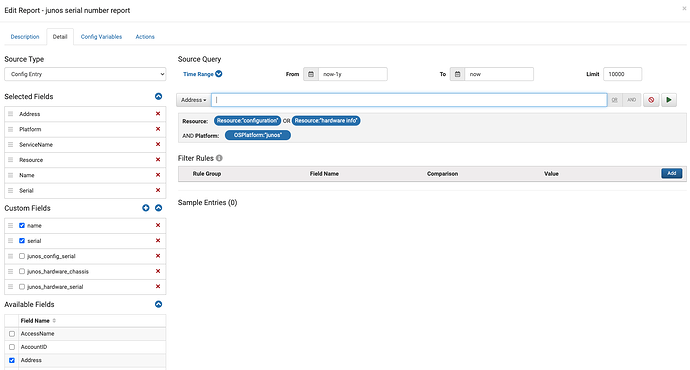
Information Extraction - Get the information you need as you need them
One of the ways SIFF differs from CMDBs and other configuration management tools is that it keeps that data in it’s natural raw form and does not try to force-fit a particular “data model”, or worse a “data model” so generic that it lacks actual useful information. We believe this to be one of the key factors that limits the promise of CMDB systems. Unlike CMDBs, SIFF does not ETL (Extract Transform Load) the collected data into a pre-defined CMDB schema. By keeping the data in its natural or raw format, we can parse and extract the required data as the the question arises rather than trying to predict what questions would be relevant for the data upfront.
For example:
- extract all the Serial number from all the Junos devices
- extract all the VRF numbers from these collection of devices
- which devices are part of these MPLS core routers
Configuration Policy and Compliance
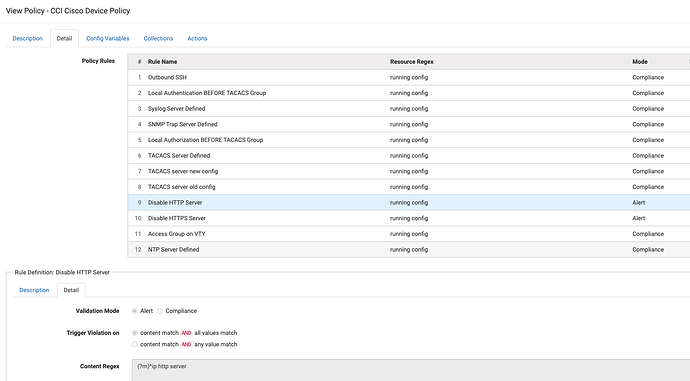
A natural extension of SIFF ability to analyze configuration data is to automate and ensure configuration best practices or security policies.
For example, the following policy define common best practices to ensure Cisco devices are configured correctly.
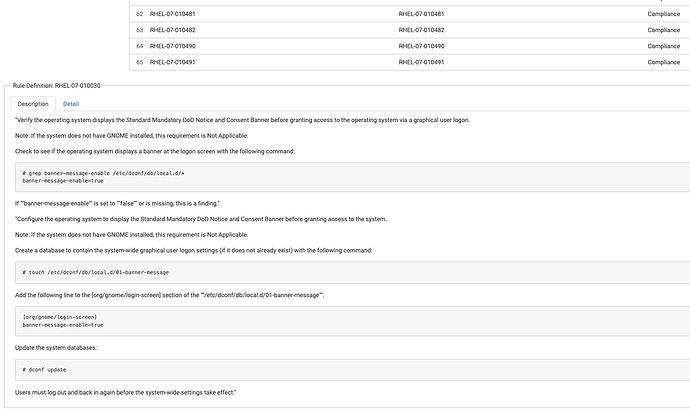
Or similarly a policy to automate and ensure DoD RedHat Enterprise Linux STIG (Standard Technical Implementation Guide) are followed
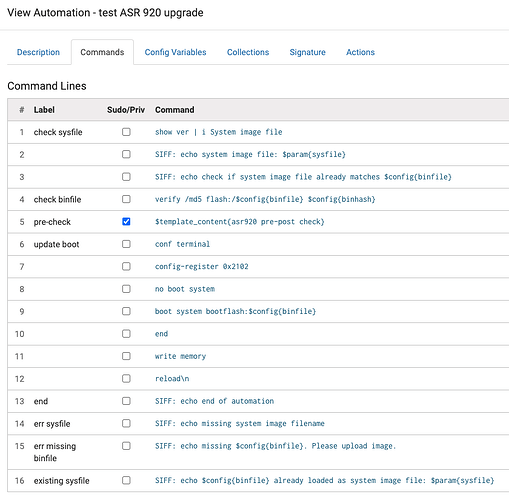
Automation configuration changes to a collection of devices
SIFF can be used to automate bulk configuration changes to multiple devices. For example upgrading the firmware on a device. The automation is designed to be as familiar as possible to the network operator by leveraging the device CLI while providing programmatic constructs through the UI, thus minimizing any coding experience. required.