Compliance policies in SIFF are very powerful and allow you to check and monitor many different configurations - or lack thereof. In this overview, we’ll use an sshd_config as an example.
Within an SSH server, there are many default values that are enabled when there is not an explicit line in the configuration to change it’s behavior. Sometimes we want to check to make sure there is not a line to override this default. For this type of check, we’ll select “content must match AND any value not match”. In this type of check, we don’t require the regex to exist which is OK - and we’ll only check the value if it does exist. If the regex doesn’t exist, then the policy is not in violation.
On the flip side, some defaults are not what we want, so we want to make sure that a line exists to override the default. For these types of checks, we’ll select “content not match OR any value not match”.
PermitRootLogin (?P<permitted>.*)
Be sure to make sure the previous character is not a # sign with a check for beginning of the line. One thing to note on regular expressions on filesin SIFF: the text is treated as one big string - which means for line-by-line regex anchor characters to work (such as ^ and $) , you need to start the regex with (?m).
(?m)^PermitRootLogin (?P<permitted>.*)
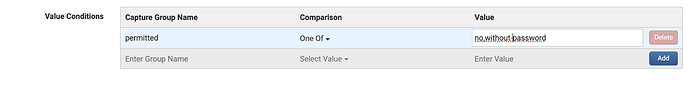
In both cases, we find need to extract a parameter’s value and test that value to verify it’s set to what we want. The value we check is out of compliance if the expression created is not true. So, if we want PermitRootLogin to always be set to “no”, we’d check that the value is “equal to” “no”. SIFF Compliance checks will create a violation when it does not match this. If you also wanted to allow without-password in the list of valid checks, you could use “One of” and “no,without-password” - separating your expected values with a comma. Finally, if you wanted to allow any settings except “yes”, you could change this to “Not equal” “yes” to allow any settings except yes - however, the use of multiple of negatives values can get really confusing :D.
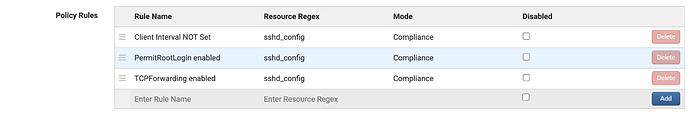
Within the compliance policy, you can create rules for all the things you want to check for this policy. For instance, you can create a Compliance policy called SSH Hardening and check lots of settings, including PermitRootLogin, AllowTCPForwarding, TCPConnectTimeout, and many others.
Once you have your Compliance Policy setup, you can activate the policy in the Policy page. When you activate this, SIFF will run the check on all active configs and you can find these in the Config page by searching for Violations. To search for all Violations, search for “*” in this field.